pagar, esperar que l’ordre s’aprovi:
Hello Miquel Urquizu,
Greetings!! We have reviewed and approved your order. Your Transaction ROR83185708M472792125. Please visit RAPIDSSLONLINE.COM and to get enrollment link details of your order.
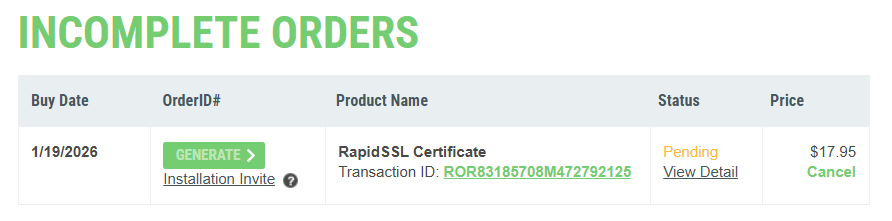
Un cop s’ha aprovat. Podem crear una sol·licitud de renovació necessitarem un fitxer beseit-net(solicitud).CSR per annexar a la sol·licitud. Aquest CSR el genera SYNOLOGY -> seguritat/certificar/acció/renovar certificat/
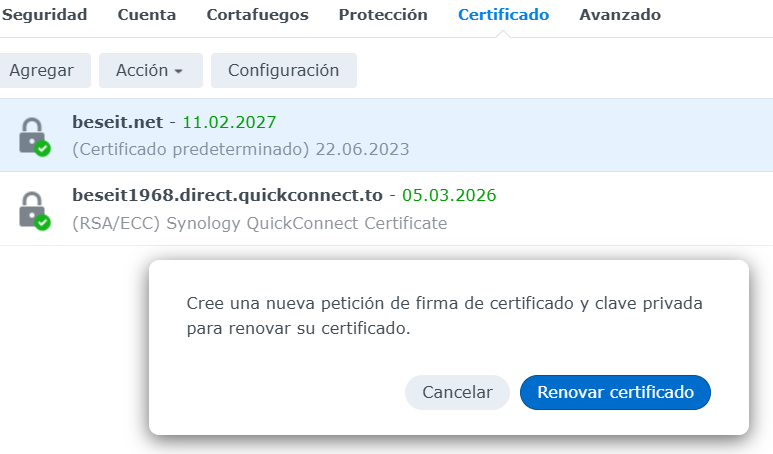
La clau es guarda per a la instal·lació NO SE ENVIA
De: orders@rapidsslonline.com <orders@rapidsslonline.com>
Enviat: dilluns, 19 de gener de 2026 12:20
Per a: urqtejmi@gmail.com
Tema: RAPIDSSLONLINE.COM Order Confirmation
| RapidSSLonline |
| Thank you for choosing RapidSSLOnline.com. We appreciate your business. Note: This charge will show as THESSLSTORE.COM in your cc statement, and as RAPID WEB SERVICES LLC on your PayPal account statement. Did you purchase an SSL and need help with the installation? Purchase our extremely affordable SSL Installation Service for only $89.99! Download A Receipt |
| Product Information: |
| Product Name Validity RapidSSL Certificate 12 |
| Customer Information: |
| Customer Name: Miquel Urquizu E-mail: urqtejmi@gmail.com Company: mut VAT Number: Address: Alegria, 24 City: Sant Cugat del Vallès State/Province: Barcelona Zip/Postal Code: 08197 Country: Spain Phone: +34936742427 IP Address: 81.0.60.36 Time: 6:20 AM [EST] Total Amount: $17.95 |
| Credit Card Information: |
| Payment Mode: Credit Card Card Number: ************9182 |
| Marina Lee Customer Experience Manager Direct : +1 (727) 388-1333 Email: marina-rapidssl@sslstore.com |
Comprovar si server.key i urquizu_info.crt enllacen
ssh urqtejmi@192.168.1.140
cd /volume1
urqtejmi@syn_beseit:/volume1/web/crt$ openssl rsa -in /volume1/web/crt/server.key -modulus -noout
Modulus=CB28376C1345D17C3F6751CAFFA270D2C1AA6C825734F969247576D321D263E425338E45FA7FD25B5AF467E68FA7537E0EE3E37099D0FAEDF02E8B7F87937849AC51EA01D69254238EC13FA415BC9D6603D26CDED9794D4AF8CBDFB0687CD04360D32514D18748D7C8410B1098C9A30C5EEFEA2BCB7388FDC117B7AF9A1E8B5AD5CF7032CC5757EFACBAA3E158C12A49168C571E5E10C950A6FBDC342DBE1E442C552580FAA43EDD9D85CDB20EA7882EEC8D2B9B6DE39BEB8A21D13A7BA81DEC7E9922A6D9068A6365246F9778A3E6DB8C54E8A0527D308F26E73D3C0D10914A51E9624AC562EFC8AF5EBC6146C3167EA24288AA9DC4B1861721D27B360EC6F1
urqtejmi@syn_beseit:/volume1/web/crt$ openssl x509 -in /volume1/web/crt/urquizu_info.crt -modulus -noout
Modulus=CB28376C1345D17C3F6751CAFFA270D2C1AA6C825734F969247576D321D263E425338E45FA7FD25B5AF467E68FA7537E0EE3E37099D0FAEDF02E8B7F87937849AC51EA01D69254238EC13FA415BC9D6603D26CDED9794D4AF8CBDFB0687CD04360D32514D18748D7C8410B1098C9A30C5EEFEA2BCB7388FDC117B7AF9A1E8B5AD5CF7032CC5757EFACBAA3E158C12A49168C571E5E10C950A6FBDC342DBE1E442C552580FAA43EDD9D85CDB20EA7882EEC8D2B9B6DE39BEB8A21D13A7BA81DEC7E9922A6D9068A6365246F9778A3E6DB8C54E8A0527D308F26E73D3C0D10914A51E9624AC562EFC8AF5EBC6146C3167EA24288AA9DC4B1861721D27B360EC6F1
també:
urqtejmi@syn_beseit:/volume1/web/crt$ bash
bash-4.4$ diff <(openssl rsa -in /volume1/web/crt/server.key -modulus -noout) <(openssl x509 -in /volume1/web/crt/urquizu_info.crt -modulus -noout)
bash-4.4$ Si no hi ha resposta és que són correctes
Si no n’hi ha cap i és nou s’ha de sol·licitar des de (sí és una renovació agregar/añadir un nuevo certificado.
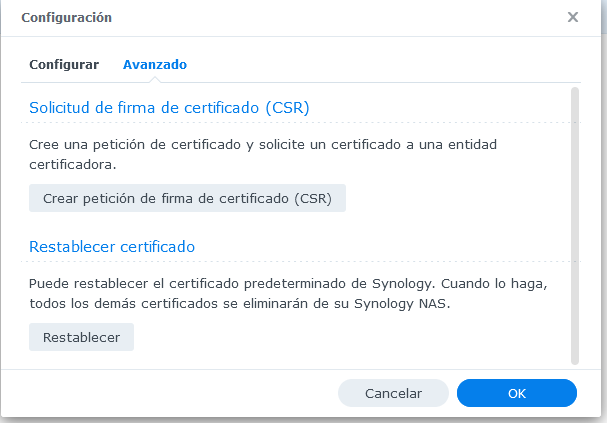
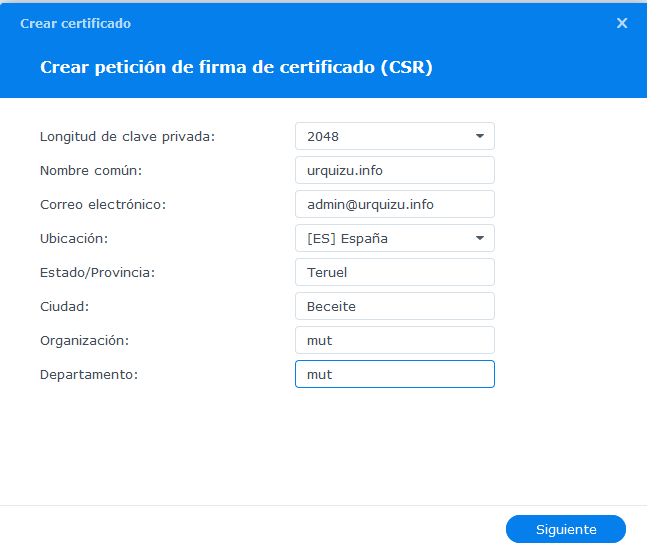
Aquest formulari de sobre és per al Synology de Beseit (certificat urquizu.info).
Anar a la web de Rapidssl
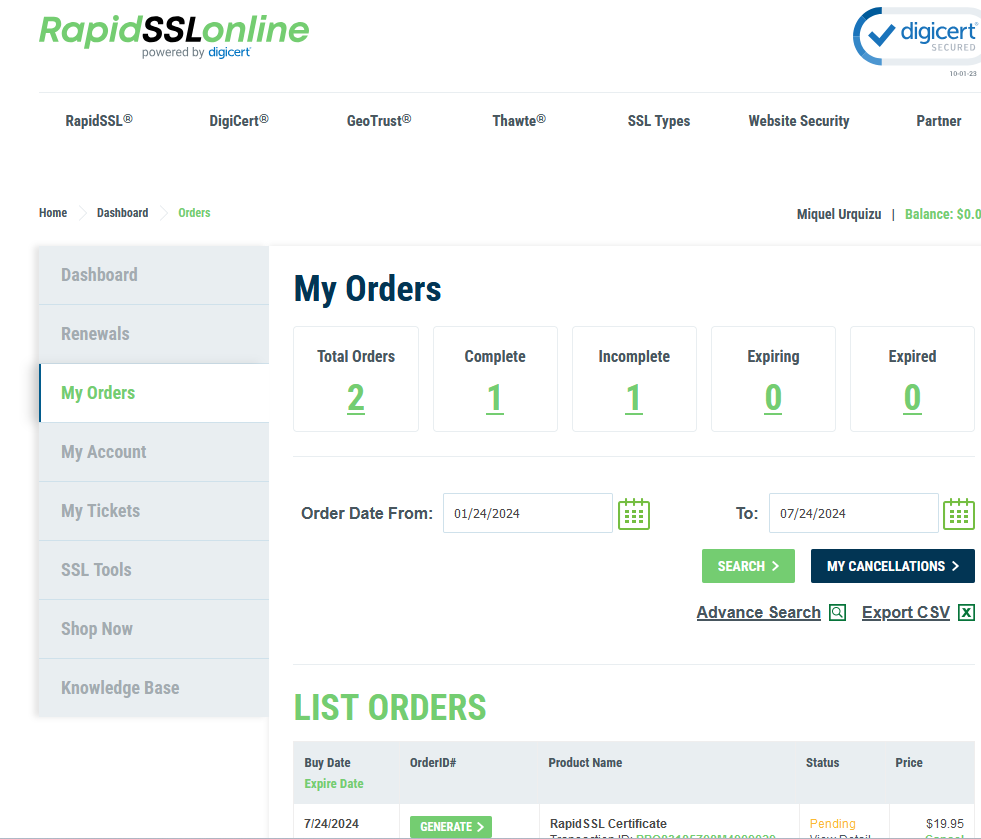
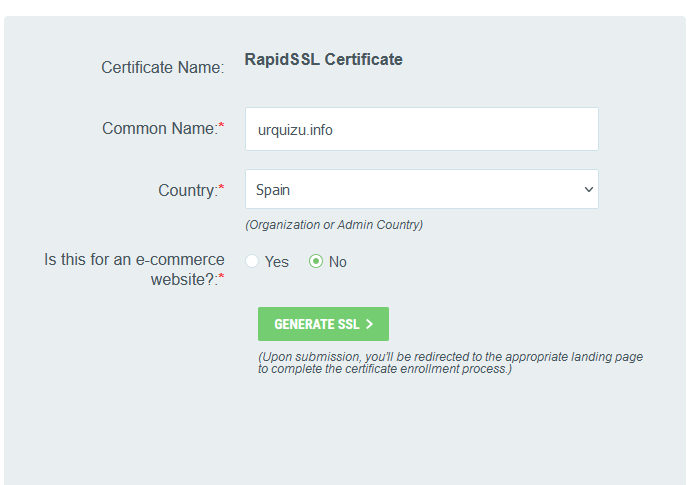
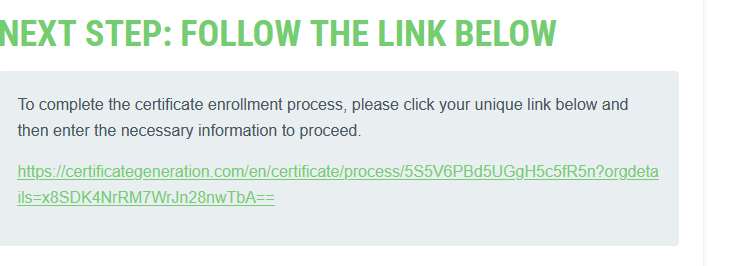
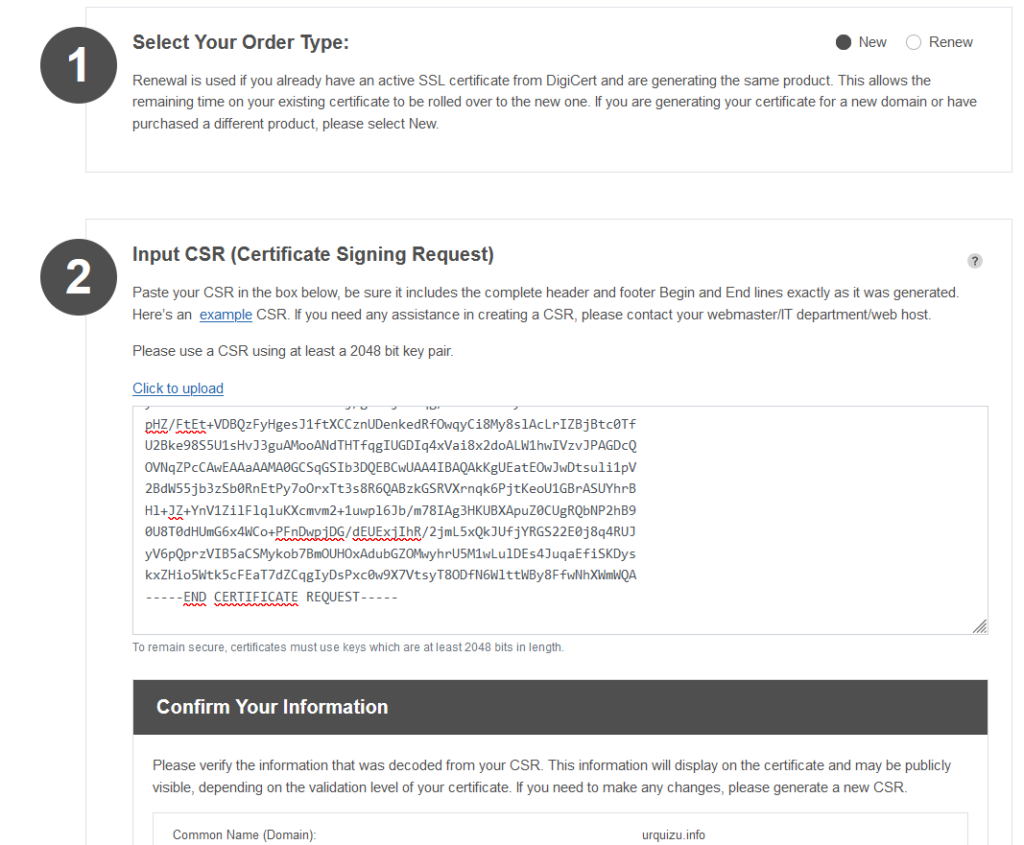
csr.pem es genera en la comanda 1. S’han de seguir els 6 passos. En acabar es guarda al directori automàticament:
urqtejmi@synology_vall:/usr/syno/etc/certificate/system/default$ dir-rw——- 1 root root 1054 Jan 15 16:48 csr.pem
Copiant el llistat que surt pel terminal Putty amb la comanda 2 i pegant al formulari es conclou el pas
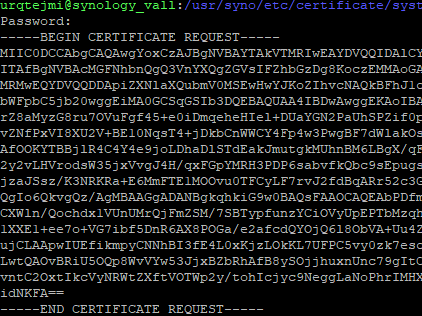
1 sudo openssl req -new -newkey rsa:2048 -nodes -keyout /usr/syno/etc/certificate/system/default/privkey.pem -out /usr/syno/etc/certificate/system/default/csr.pem
2 sudo cat /usr/syno/etc/certificate/system/default/csr.pem
urqtejmi@synology_vall:~$ sudo openssl req -new -newkey rsa:2048 -nodes -keyout /usr/syno/etc/certificate/system/default/privkey.pem -out /usr/syno/etc/certificate/system/default/csr.pem
Password:
Can't load /root/.rnd into RNG
139729879611200:error:2406F079:random number generator:RAND_load_file:Cannot open file:crypto/rand/randfile.c:98:Filename=/root/.rnd
Generating a RSA private key
.............+++++
.........................................................................+++++
writing new private key to '/usr/syno/etc/certificate/system/default/privkey.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [TW]:ES
State or Province Name (full name) [Taiwan]:Barcelona
Locality Name (eg, city) [Taipei]:Sant Cugat de Valles
Organization Name (eg, company) [Synology Inc.]:MUT
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address [product@synology.com]:mut@gmail.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
urqtejmi@synology_vall:~$
Rebem Email a admin:
Tras clic al link la orden s’activa
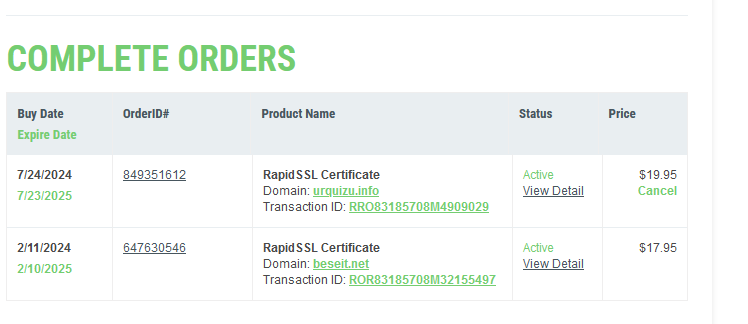
tras clic a detallas
Good day,
Thank you for your email.
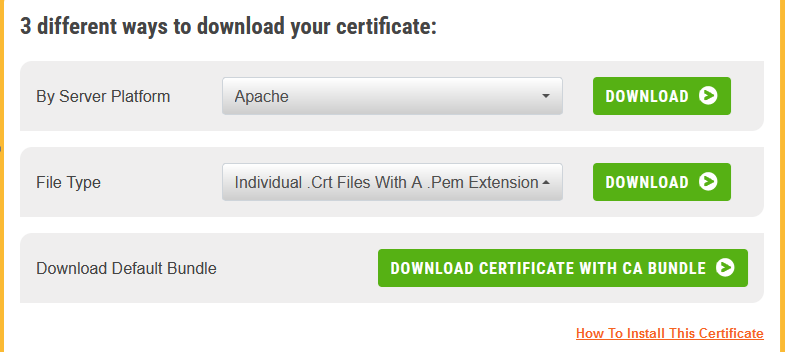
As per one of the screenshots you shared:
You can download your certificate in the .pem format if you choose the first of those option you will get one file that should include all three certificates. The second/middle certificate would be the intermediate certificate.
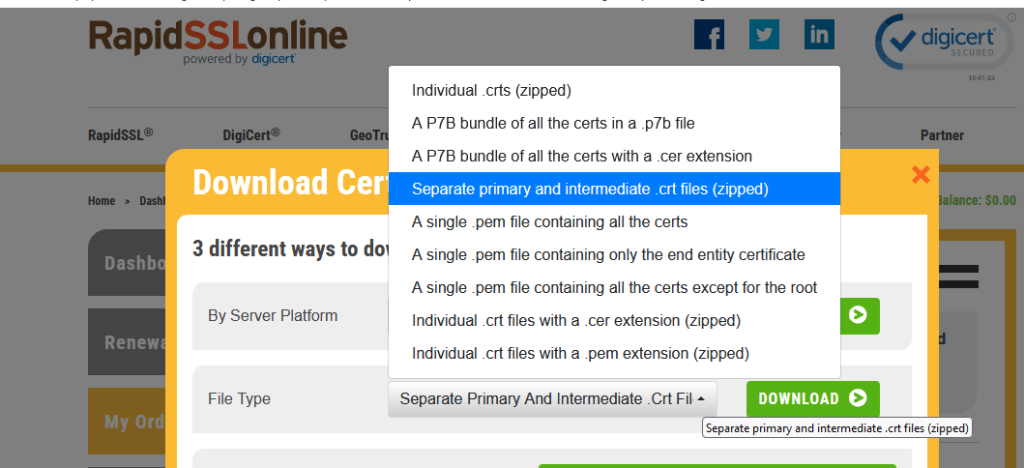
OBRIR PUTTY
Certificats guardats a Synology:
urqtejmi@synology_vall:/usr/syno/etc/certificate/system/default$ dir
total 44
drwxr-xr-x 2 root root 4096 Jan 14 18:58 .
drwxr-xr-x 4 root root 4096 Jan 11 10:39 ..
-r——– 1 root root 2537 Jan 9 19:46 cert.pem <-beseit_net.cer
-r——– 1 root root 1692 Jan 9 19:46 chain.pem
-rw——- 1 root root 1017 Jan 14 18:58 csr.pem
-rw——- 1 root root 0 Jan 14 17:17 fixed_privkey.pem
-r——– 1 root root 4229 Jan 9 19:46 fullchain.pem
-rw——- 1 root root 240 Jan 9 19:46 info
-rwx—— 1 root root 1708 Jan 14 18:56 privkey.pem
-rw-r–r– 1 root root 1294 Jan 9 19:46 root.pem
-rw-r–r– 1 root root 1692 Jan 9 19:46 short-chain.pem
Lista info
sudo cat /usr/syno/etc/certificate/system/default/info
Llista cert
sudo cat /usr/syno/etc/certificate/system/default/cert.pem
sudo cat /usr/syno/etc/certificate/system/default/privkey.pem
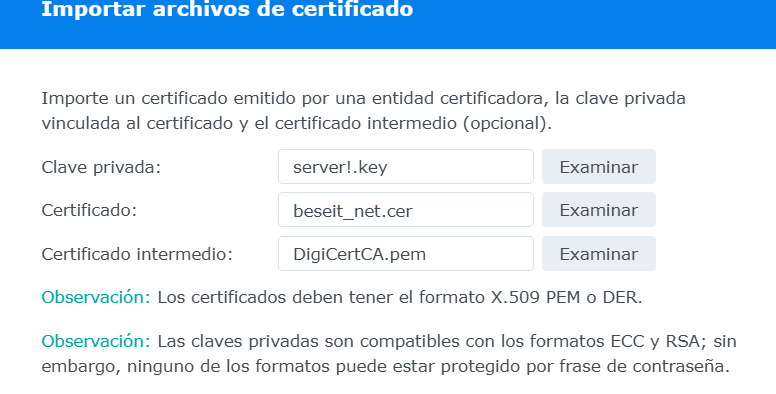
Llista cert
sudo cat /usr/syno/etc/certificate/system/default/cert.pem
Download Pem extension com indica la imatge d’amunt!!
Els certificats: beseit.net, server.key, intermediate es guarden a: urqtejmi@synology_vall:/usr/syno/etc/certificate/system/default$ sudo cat /usr/syno/etc/certificate/system/default/cert.pem = beseit.net
COMPROVACIÓ DE CLAUS
sudo openssl req -new -newkey rsa:2048 -nodes -keyout /usr/syno/etc/certificate/system/default/privkey.pem -out /usr/syno/etc/certificate/system/default/csr.pem
LListad del directori:
ls -l /usr/syno/etc/certificate/system/default/
urqtejmi@synology_vall:~$ ls -l /usr/syno/etc/certificate/system/default/
total 36
-r-------- 1 root root 2537 Jan 9 19:46 cert.pem
-r-------- 1 root root 1692 Jan 9 19:46 chain.pem
-rw------- 1 root root 1017 Jan 14 18:58 csr.pem
-rw------- 1 root root 0 Jan 14 17:17 fixed_privkey.pem
-r-------- 1 root root 4229 Jan 9 19:46 fullchain.pem
-rw------- 1 root root 240 Jan 9 19:46 info
-rwx------ 1 root root 1708 Jan 14 18:56 privkey.pem
-rw-r--r-- 1 root root 1294 Jan 9 19:46 root.pem
-rw-r--r-- 1 root root 1692 Jan 9 19:46 short-chain.pem
urqtejmi@synology_vall:~$
el hash (cheksum)
sudo openssl rsa -in /usr/syno/etc/certificate/system/default/privkey.pem -pubout -outform DER | openssl md5
urqtejmi@synology_vall:~$ sudo openssl rsa -in /usr/syno/etc/certificate/system/default/privkey.pem -pubout -outform DER | openssl md5
writing RSA key
(stdin)= 688854cededb762e53bdeee4747adb0d
el terme "hash" és sovint utilitzat com a sinònim de "checksum". Tots dos termes es refereixen a un valor generat a partir d'un conjunt de dades que serveix per verificar la integritat d'aquestes dades. Els algorismes de hash, com MD5, SHA-1 o SHA-256, són comunament utilitzats per generar aquests valors.
urqtejmi@synology_vall:/usr/syno/etc/certificate/system/default$ sudo openssl rsa -noout -modulus -in privkey.pem | openssl md5
(stdin)= 3661baaf0013c5523ce7de56754c1a12
urqtejmi@synology_vall:/usr/syno/etc/certificate/system/default$
Què és server.key i privkey.pem?
server.key: Sovint és el nom que se l’encerta privada en entorns de servidor. Conté la mateixa informació queprivkey.pem.privkey.pem: És el format de la clau privada utilitzat pel sistema Synology. Tècnicament, és el mateix tipus de fitxer queserver.key.
Per què no són exactament iguals?
El problema pot sorgir per una de les següents raons:
- Format diferent:
Alguns sistemes esperen que la clau privada estigui en un format RSA simple (sense etiquetes PKCS#8). Siprivkey.pemestà en format PKCS#8, el Synology pot no acceptar-lo directament. - Contingut modificat:
Si s’ha regenerat la clau privada o s’ha manipulat d’alguna manera, el hash resultant serà diferent i el certificat ja no serà vàlid per a aquesta clau.
Solució: Generar un server.key a partir de privkey.pem
Si el sistema demana específicament server.key, pots copiar o convertir privkey.pem al format que s’espera. Prova el següent:
1. Comprovar el format de privkey.pem
Executa:
bashCopia el codisudo openssl rsa -in /usr/syno/etc/certificate/system/default/privkey.pem -check
- Si això mostra detalls de la clau privada (i no errors), ja és una clau RSA simple.
2. Copiar privkey.pem com server.key
Pots simplement fer una còpia amb el nom esperat:
bashCopia el codisudo cp /usr/syno/etc/certificate/system/default/privkey.pem /usr/syno/etc/certificate/system/default/server.key
3. Convertir al format RSA simple si cal
Si privkey.pem no està en el format correcte, converteix-lo:
bashCopia el codisudo openssl rsa -in /usr/syno/etc/certificate/system/default/privkey.pem -out /usr/syno/etc/certificate/system/default/server.key
Aquest comandament guarda una versió RSA simple de la clau com server.key.
4. Reinicia el servei
Un cop copiades o convertides les claus, reinicia el servei web del Synology per aplicar els canvis:
bashCopia el codisudo synoservicecfg --restart nginx
Comprova si el certificat funciona
Després d’aquests passos, verifica que el certificat funciona correctament accedint al lloc web o al servei que utilitza HTTPS. Si no, assegura’t que el certificat i la clau privada coincideixen (comprovant els seus hashes).
If you want it separate you can always open a text editor and copy and paste it from the main file onto a separate file to save it.
I hope that the above will assist, if further assistance is required please don’t hesitate to reach out.
Nicole
DigiCert Support
We are constantly looking for ways to improve our customer experience and would love to hear your feedback. Click Here for Survey or you can email my manager directly at: ts_manager@digicert.com
Thank you from the DigiCert Support Team!